Phishing attacks and spoofed email scams aren’t going away anytime soon – last year, they were responsible for 94% of successful malware attacks! And because of their reliance on social engineering, they’re remarkably difficult to stop with software or hardware defenses alone. That’s why one of your best defenses is learning the key signs of a digital scam.
In our recent webinar, we took a closer look at three real-world examples of phishing attacks, and dissected how each one preys on the psychology of email communication. Although each example is different in its own way, all three prey on an appeal to authority and a sense of urgency to get what they want. Check out our recorded session for the full story, or keep reading below for some key takeaways!
Example 1 – The CEO
One very common tactic that bad actors like to employ is pretending to be your company’s CEO. This approach has a few advantages: it appeals to the target’s sense of authority and their sense of urgency – because what’s more important than a direct email from company leadership? That perceived urgency can get a target to overlook many small discrepancies, and often that’s all a scammer needs.
This type of impersonation is often quite easy to pull off, because CEOs are often the most well-known staff member featured on your organization’s website or in online company profiles. It’s much harder to comb through LinkedIn for your direct supervisor’s name, but the CEO is both easier to identify and more likely to get your attention.
-1.png?width=750&name=Phishing%20Email%201%20(1)-1.png)
So let’s say they HAVE gotten your attention, and you’re looking at the email above, which claims to be from Lyf Wildenberg, Mytech’s President & CEO. Although it seems to be urging swift (and confidential) action, a bit of extra attention here will go a long way.
Although the email sender’s name says “Lyf Wildenberg,” the actual email address is something completely irrelevant. That’s because scammers can put whatever they want in the “name” space of an email, even though imitating the email address itself is much more difficult (but not impossible – see Example 3 below for one such attempt!). A legitimate email from your CEO is much more likely to come from a company email address, so anything outside of this ought to be a red flag.
In instances like this – or even when the domain name is correct but the message is suspicious – the golden rule of phishing security applies: seek confirmation through a different, official channel. Preferably in person: call your CEO and ask if they gave you this request. Phishing relies on urgency to keep you from questioning the instructions, so a single pause to double-check can stop a scam dead in its tracks.
Example 2 – The Post Office
Other, broader-reaching phishing campaigns will impersonate commonplace services used by millions of people. The advantage of this attack is that it’s even easier to pull off than CEO impersonation, because it doesn’t have to distinguish between victims. Simply pick a service that gets people’s attention – say, an organization that delivers important packages every day – and send the email to your entire list of targets.
The United States Postal Service is a perfect example, because few things are more compelling than a package delivery. Because so many people have packages in the mail at any given time, it turns into a simple numbers game: send to enough people, and someone’s going to be expecting a package when they get an email about a failed delivery!
-1.png?width=1200&name=Phishing%20Email%203%20(1)-1.png)
Like the CEO example, this phishing attack also simulates legitimacy and authority: long strings of numbers and package codes, which the target is highly unlikely to verify. It even features the USPS logo, and offers a link to reschedule your delivery! However, clicking that hyperlink at the end can take you any number of places…none of them good.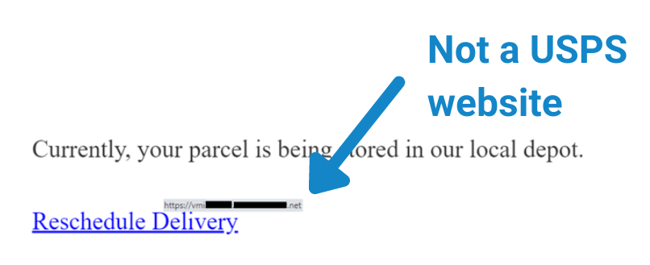
Again, the same trademark warning signs are here. The name says “USPS” but the actual address is a suspicious hotmail.com account. Likewise, the hyperlink claims to link to the United States Postal Service, but if you hover your cursor over the link (WITHOUT clicking it!), it actually displays something completely different – often a long, convoluted URL that would lead you to a malicious site.
Example 3 – OneDrive
In the same vein as Example 2, this phishing attack impersonates a legitimate organization – this time, OneDrive. It even seems to request an important, work-relevant action from you, which you can only take for a limited amount of time. And even worse, this email has been spoofed to look exactly like a legitimate sender!
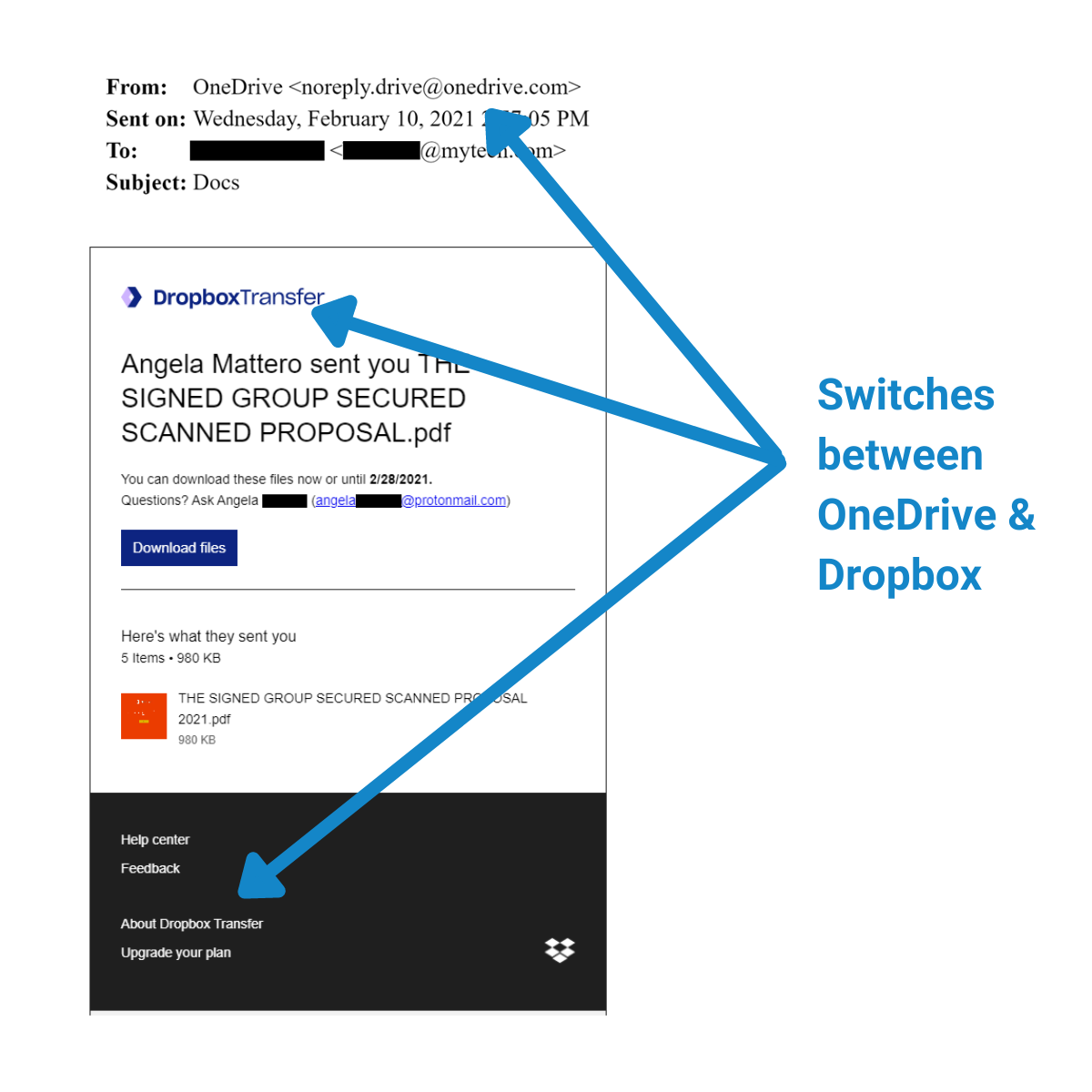
As you can see, this attack is far more polished, and carefully designed to simulate a real business email. It even switches between Dropbox and OneDrive by mistake, but if you're not reading closely, you won't catch the discrepancy. Most people skim over all the text on a download link email, as long as it LOOKS official. However, the same precautions still apply.
-1.png?width=650&name=Phishing%20Email%204%20(1)-1.png)
If you take a second to examine the link before clicking, you can see it’s not really a OneDrive domain name – or even any legitimate site! The URL is for some completely random destination, designed for malicious purposes and disguised as a legitimate link to download an important pdf. Despite many of the classic red flags being cleverly hidden, you can still catch this phishing attempt by its trademark urgent messaging and insistence on taking some sort of action -- especially one that comes as a surprise.
For both of these “company” phishing attacks, the defense is the same: confirm the information through other, legitimate channels. Log into your OneDrive account, or check your incoming packages on the USPS site. If they’re legitimate messages, you will be able to do whatever is necessary through the company’s original site. Phishing attacks will try to make you think the link in this email is the only fix for the problem, but this simply isn’t so.
Key Takeaways
You may have noticed something about these scams: there were no million-dollar promises, no poorly-spelled sentences, and no exiled princes offering to share their inheritance. While that category of scam email still exists, more complex and targeted attacks go out every day. It’s not enough for something to “look legit” anymore, because bad actors have gotten quite good at meeting that standard, too.
However, the defense for every phishing scam – no matter how complex – remains the same: nothing. When you get an urgent request you weren’t expecting, don’t do anything they tell you to do, and don’t reply to the message. If you feel the message might hold a grain of truth, you can reach out through a different method (like the company’s website or portal, or by calling the main company’s phone number). If you suspect a message constitutes a phishing attack, notify your IT team so they can take precautionary steps to block future attempts.
But it’s not enough for you to know what to do. Because these attacks target the weakest link in a chain, the only way to effectively defend your entire organization from phishing attacks is to give every member of your team the understanding and awareness necessary to stop phishing attempts in their tracks. That’s why, unlike most MSPs, Mytech provides regular Security Awareness Training to its clients. More than just a single orientation video, this robust series of videos and simulated attacks will prepare your team to defend against targeted phishing attacks…no matter when or where they appear.

