It happened. Your business just suffered a cybersecurity attack. It’s easy to feel somewhat helpless after your organization has been terrorized by a security breach, but you don’t have to feel like a sitting duck for the next one.
Whether it was a major incident or an isolated occurrence, chances are you are ready to invest in mitigating an attack from happening again.
While most SMB business owners will say that they are concerned about their information security risks, more than half (51%) of those organizations are not allocating any budget/time to mitigating those risks! It isn’t until after a breach occurs that many businesses really review their information security posture.
Most articles you'll find regarding steps to take following a breach are about the standard crisis management steps a business should go through.
- Confirming A Breach Occurred
- Securing Your Operations
- Fixing Immediate Vulnerabilities
- Notifying Appropriate Parties
- etc.
While these steps are crucial to ensuring you can recover from the breach, we want to talk about the most important step…. future vulnerabilities.
Recovering from a security breach takes an immense amount of time, money, and resources from your organization. Because of this, many organizations don’t finish the last step of assessing their vulnerabilities and making a plan to start addressing them. But this is the most important step to help prevent a security breach from happening again, or at least make it far less painful next time.
Assess & Document
We know, you probably just spent a tremendous amount of time and money to get your organization back and the last thing you want to do is “relive” the chaos the security breach caused. However, by assessing the damage, the true impact (cost) to your organization, as well as documenting the processes you just developed (even if they were “on-the-fly”), you’ll have a great start to your future information security policy.
- Assessing the True Impact to your Organization - By understanding the true impact the breach had on your organization you’ll be able to make a more informed decision on the future of your information security (cyber-security) policies. Many business leaders tend only to quantify the tangible costs, such as ransomware costs, regulatory fines and/or legal fees, costs of notifying customers and/or providing security monitoring services, and more. But these costs sometimes are just the tip of the iceberg. Many factors such as business downtime resulting in time and productivity loss, loss of intellectual property, brand degradation, and insurance premium increases are much harder to quantify, and typically have a more significant impact.
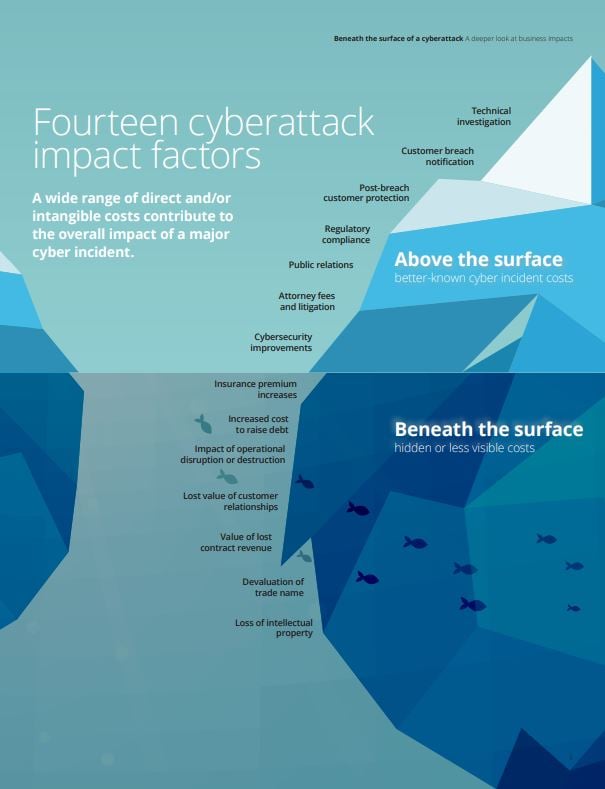
*Deloitte Advisory’s Cyber Risk Services, “Beneath the surface of a cyber attack: A deeper look at business impacts”
- Document Your Recovery Steps - Chances are you didn’t have an incident response policy or procedure prior to being breached. And while the process you just went through to recover may have been rudimentary at best, it’s a start! It’s a good idea to document what you did while everything is fresh in your head. Document the who, what, when, and if possible, include a post mortem. What went well, what could have gone better, what holes still exist?
Don’t Just Throw Money At Your Security Vulnerabilities
Many times, after an organization has suffered a security breach, the fear of another one can lead executives to make somewhat irrational decisions. Sometimes this results in investing in ‘quick fix’ security solutions that end up costing a lot of money but don’t really fix the problem. And unfortunately, many organizations are willing to take advantage of that pain just to sell you something.
Evaluate where you believe your biggest risks are. Whether your breach was an internal technical vulnerability such as a missing patch or update, a personnel vulnerability such as phishing or ransomware; or the breach was a result of a physical attack such as a stolen laptop or key fob, your natural instinct will be to plug that hole first. However, it may not be your biggest vulnerability. You may not even know where to start — hiring a 3rd party risk analysis or assessment team may be your first order of business. Finally, review your budget to allow investing in decreasing your risk in those key areas.
Be Realistic
You can’t fix all your security vulnerabilities overnight. Deploying the proper security tactics requires a healthy mix of time and financial investment. Providers that urge you to invest too much up front or too little over too long are not looking out for your best interest. Your information security should be a part of your long-term strategy; therefore, part of your annual IT budget and plan.
So how do you realistically prioritize?
- Prioritize Core Business Processes - Start by identifying the core business processes that, would significantly disrupt business functions. Decide which impairments would be catastrophic, and which would be classified as more of a nuisance. List them in order of impact.
- Identify Applications and Assets that Support Those Processes - Next, identify the applications and business assets that support those processes. For example, an e-commerce re-seller may not be able to conduct business if their domain name was stolen, or if their website was compromised.
- Estimate the Various Costs of an Attack - This will be hard to do because there are so many variables. Now that you have been through an attack, and you have identified the true associated cost, try your best to estimate the organizational cost of each risk scenario identified.
- Estimate the Cost to Secure the Vulnerability - Do some research to estimate what it would cost to mitigate the risk of each identified scenario. We all have limited budgets, and understanding the estimated cost to mitigate the risk will help you better prioritize your next steps.
With this information, you should be able to create a realistic plan to start mitigating your organization’s risks. Keep in mind; your plan needs to balance the impact and cost of an attack against the time and cost to mitigate the risk. Don’t fix a $5.00 problem with a $20.00 solution.
Do You Have The Right Team?
At this point, you may be feeling overwhelmed. The technology and security of your organization are complex, and you may be wondering if you have the right team of resources for the modern cyber-security landscape. Whether your IT department is in-house, or you subscribe to managed IT services, you’ll want to ensure your team has the knowledge, expertise, time, and skill-set to help you assess, build, and execute your information security goals.
Remember, your information security is not just a technical challenge. Too often, the decisions regarding the security of the organization are left to the IT manager or consultant who does not possess the deeper understanding of the business’s operations. A mature managed services consultant or IT analyst will have the business acumen necessary to provide recommendations that truly encompass the entire organization’s risk.
As the cyber-security landscape continues to evolve, you’ll never be 100% protected from another security breach or attack. However, understanding your organization’s risks, and having a plan to continually improve your security posture,will not only better protect you, but it will also help you recover faster and with far less impact to your organization.


