We're on your side, we promise.
Our mission is to Make IT Easy for our clients, and many of our solutions fall under that umbrella. From high-quality security software, to an expert team of technicians, to a comprehensive approach to hardware and infrastructure, we’ve committed plenty of resources to improve your IT experience.
So if we are, in fact, on your side, why do we routinely “phish” your end-users with misleading or deceptive emails? And why do we consider this a crucial & beneficial service?
To put it simply: because you need to know what to expect.
Like a fire drill -- for email
Think about all the skills you’re trained to do. Job functions, cooking, laundry, driving a car, riding a bike, playing a sport or a musical instrument – anything that took work to learn. You didn’t just see a car for the first time and get on the interstate that same day; you spent a long time learning how to use it, in a safe & controlled environment.
But what about truly dangerous things? Most of us have never been in a burning building, but we’re all somewhat familiar with how to escape one. That’s because, since the 1950s, our schools have held regular fire drills – a simulated high-risk scenario – to test students’ reactions and train them on the proper procedure to escape.
Our simulated phishing campaigns share the same objective, by creating a highly-convincing email (seemingly from a reputable company or service) that prompts your team members to interact in some way. Our goal isn’t to fool as many of your end-users as possible: our goal is to build their experience and teach them what to expect. By seeing these examples, your team will hopefully get a better picture of what threats exist – and how to recognize them.
Taking it seriously
For many people, those school-year fire drills were more of a nuisance than a source of fear. And many tech-savvy folks look at phishing emails the same way. We’ve all heard of “Nigerian prince” scams: outlandish spam emails with plenty of typos and fantastical stories that promise you millions of dollars. Plenty of these low-effort campaigns circulate constantly, and they’re fairly easy to spot.
But some aren’t. Some phishing campaigns are highly-polished, clever, articulate, and even topical. Imagine this hypothetical: it’s December and the boss has been talking about bonuses, and then you get an email about bonuses. A nonprofit you support sends an email, seeking your signature for an issue that recently gained media attention. Your company had a rough quarter, and then you get an automated email from your HR portal…
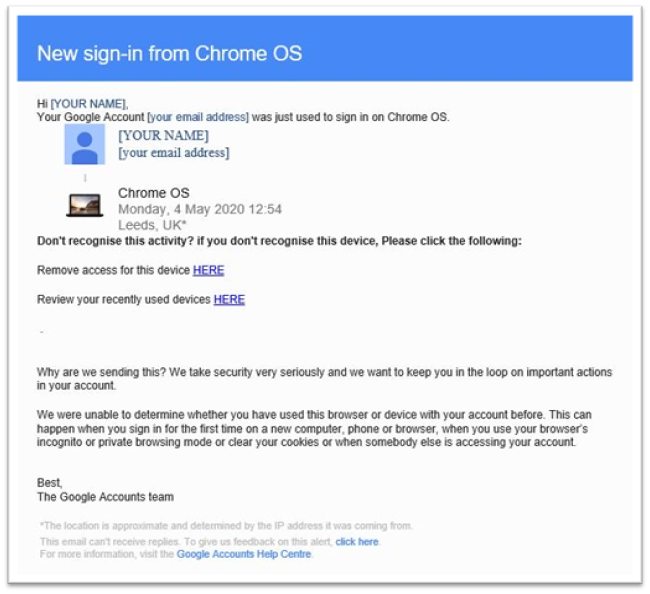
One click on a malicious link is all the foothold that’s needed. You don’t have to give your login credentials, your Social Security Number, your credit card, anything at all – you just have to click once. If you’re not prepared for something that looks so official, or if you don’t know to check a hyperlink, or if you subconsciously think that clicking it “just to see” isn’t a big risk, then a highly-polished phishing email can catch you by surprise.
In fact, our simulations alone catch quite a few people. We simulate a new phishing campaign for our clients every month, and every month, somebody clicks that link. Our work won’t be done until every one of our clients’ end users can spot – and report – these phishing emails.
Lines we won't cross
Real hackers don’t play fair. As we discussed above, they’ll exploit dirty tricks and sore spots to get what they want. They know when recessions are happening. They know where outbreaks or natural disasters are hitting hardest. They know when volatile social issues are on everyone’s minds. They’ll use those tactics, and they won’t think for a second whether it causes anybody any pain.
As our clients’ trusted partner, we won’t cross those lines. We hope to train and prepare our clients’ end-users, but not if it causes undue distress or “pours salt in the wound” on a difficult subject. After all, your teachers wanted you to be prepared for an emergency, but they never actually set the building on fire to test their students…or so we hope!
To that end, we have certain rules about the subject matter of our phishing tests. It’s an evolving list, and it changes as new threats circulate and clients offer feedback, but in general it follows several guidelines:
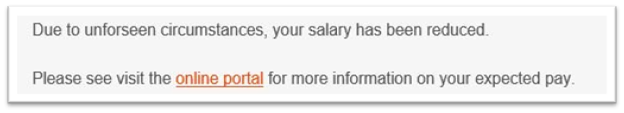
- Our tests won’t target compensation or job status (pay reductions, layoffs, bonuses)
- Our tests won’t employ grief-based emotional manipulation (family loss, suicide, or mental health)
- Our tests won’t exploit social justice issues (racism, gender, sexuality)
- Our tests won’t reference public emergencies (COVID-19, civil unrest, natural disasters)
It's a security partnership
Again, even though we won’t use certain subject matter in our simulated phishing campaigns, malicious actors will. Our Security Awareness Training is a critical training resource about those recent manipulative campaigns & tactics…but we can only provide the tool. It’s up to you and your end-users to take that knowledge and do something with it.
Mytech has a host of security features and resources, but at the end of the day our work must be a collaboration with you – we call ourselves “Mytech Partners” for a reason, after all. Your internet security relies on you, and your willingness to keep informed & savvy to the latest cybersecurity threats. In doing so, you can shore up your company’s most critical layer of protection: you.

