As of yet, there is no patch available that completely eliminates the vulnerability, so currently the best defense is user awareness. This exploit requires user input, which can take the form of opening, downloading, or accessing a malicious Microsoft Office file sent by an attacker. Even a single click of an infected file can be enough to execute the malicious code.
What you should do:
The bad news: this exploit requires user input. The good news: this exploit requires user input! If your team members have experience detecting a phishing attempt, they are well-positioned to stop this attack in its tracks. Please notify your team of this vulnerability for Office files, and remind them that they should never click, open, download, or even preview an email attachment that they were not expecting to receive.
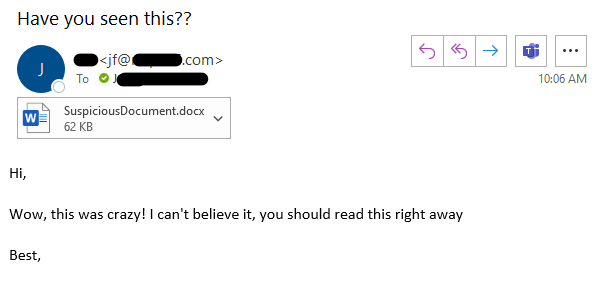 That special mention of “previewing” is critical for this exploit. Unlike other vulnerabilities, it doesn’t require approval from the “enable macros” or “enable editing” popups. Simply clicking the attachment, which opens it in an Outlook or Explorer preview window, is enough to execute the malicious code (see example below).
That special mention of “previewing” is critical for this exploit. Unlike other vulnerabilities, it doesn’t require approval from the “enable macros” or “enable editing” popups. Simply clicking the attachment, which opens it in an Outlook or Explorer preview window, is enough to execute the malicious code (see example below).
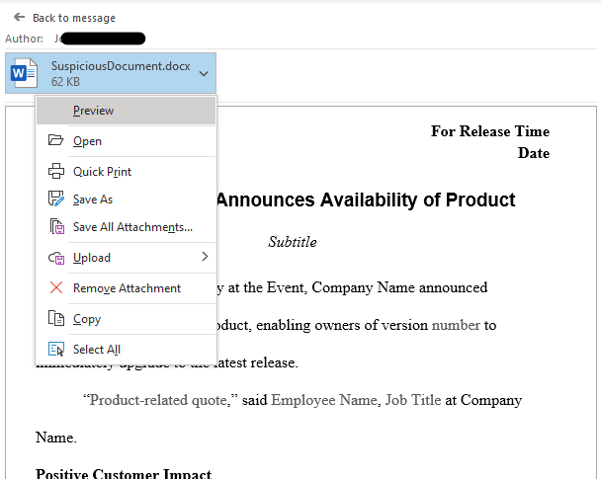
Encourage your team to suppress their curiosity and avoid clicking any unexpected files…not only until this vulnerability is patched, but also as a general rule!
What Mytech is doing:
As soon as the patch is available from Microsoft and confirmed safe to deploy without disruption, Mytech will roll it out to our clients. In the meantime we have implemented several mitigations for our fully managed clients, like deploying email defense to intercept malicious attachments, and turning off certain permissions to limit the damage they can cause. We also employ numerous backend tools to monitor for exploits just like this one, and will be watching diligently for any indicators of compromise (IOCs).
There is no “complete” workaround for this exploit, though, so until the patch is deployed the best way you can protect yourself is by putting your team on guard for phishing attempts. Follow our Security Alerts page for future updates, and read our blog post “Catching a Phish” for some simple tricks you can share with your staff to keep them aware and secure.

